In our ever more digital world, traditional payment methods are being replaced by secure and efficient alternatives. Apple Pay has taken a leading role in this transformation, providing a hassle-free solution for making transactions via Apple devices. Not only is it convenient, but Apple Pay also puts security and privacy front and center, ensuring trust and reliability during modern transactions.
How Apple Pay Works
Contactless payments are made possible by the technology known as near-field communication (NFC), which Apple Pay utilizes effortlessly. With your Apple device held close to a payment terminal, transactions can be swiftly and securely completed.
Apple Pay is compatible with a range of Apple devices, such as iPhones, iPads, Apple Watches, and Macs. These devices harmoniously collaborate to deliver an uninterrupted and smooth payment experience.
Strong Encryption
End-to-end encryption lies at the core of Apple Pay’s security measures, shielding your valuable payment details. With every transaction, your card information undergoes a transformation, generating an exclusive code that can only be used once. As a result, your sensitive data is never exposed or retained in its original format.
Thanks to this advanced encryption technique, even if a payment terminal faces infiltration by ill-intentioned individuals, the captured data proves futile for potential attackers.
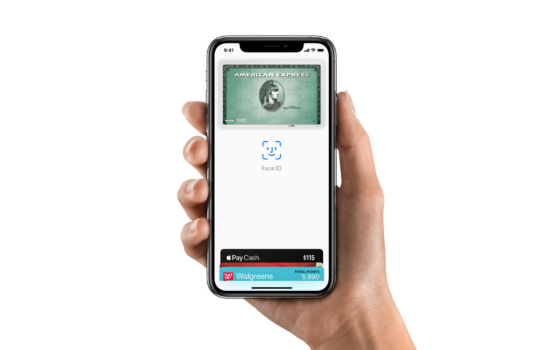
Device Security
To authorize payments, Apple Pay utilizes the security features of your device, such as Touch ID and Face ID. These biometric authentication methods offer an extra level of security beyond regular passwords. Even if someone manages to gain unauthorized access to your device, without your biometric approval, they are unable to make any payments. This significantly enhances the overall security of your transactions.
Tokenization and Unique Device Numbers
When using Apple Pay, a process called tokenization is employed to safeguard your card details. Instead of sharing your actual card number with merchants or storing it on your device, a unique token is generated. As a result, any stolen tokens have no value for future transactions. The similar technology is used when you play slots online with cryptocurrencies – the practice of utilizing blockchain. By implementing this method, unauthorized individuals are prevented from exploiting your card information.
Biometric Authentication
The inclusion of biometric authentication methods, such as Touch ID or Face ID, adds a personalized layer to security. By utilizing your unique fingerprint or facial features, these methods serve as a distinctive identifier for approving payments.
The presence of biometrics significantly diminishes the possibility of unauthorized individuals gaining access to your device and executing unapproved transactions. Only your distinct biological traits can unlock payment authorization, ensuring enhanced protection for your financial transactions.
In Summary
In a rapidly evolving digital world, security and privacy are paramount, especially when it comes to financial transactions. Apple Pay rises to the challenge by integrating robust security measures that ensure the protection of your sensitive information. From strong encryption and device-level security to tokenization and biometric authentication, every facet of Apple Pay is designed with the user’s security and privacy in mind. As you embrace the convenience of contactless payments, you can rest assured that Apple Pay is not just a transaction method but a shield of protection for your financial interactions.